by compit | Dec 6, 2016 | Archived Articles
What are the main challenges faced by MSPs? How would you overcome them? · Educating clients and prospects on transitioning to the Cloud and the pros and cons, this works both ways, some clients may be very reluctant about the security “where is my data” whilst...

by compit | Nov 30, 2016 | Archived Articles
I’ve mentioned the evasion tactics that ransomware uses more than once in previous blog posts. This collection of technical methods ensures that crypto-ransomware infections can stay below the radar and: Not get picked up by antivirus products Not get discovered by...

by compit | Nov 24, 2016 | Archived Articles
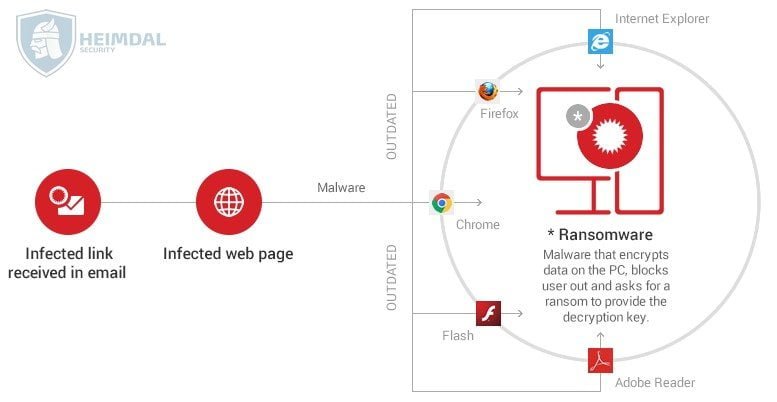
Though the infection phase is slightly different for each ransomware version, the key stages are the following: Initially, the victim receives an email which includes a malicious link or a malware-laden attachment. Alternatively, the infection can originate from a...

by compit | Nov 15, 2016 | Archived Articles
Ransomware and any other advanced piece of financial or data stealing malware spreads by any available means. Cyber criminals simply look for the easiest way to infect a system or network and use that backdoor to spread the malicious content. Nevertheless, these...

by compit | Nov 9, 2016 | Archived Articles
We all know businesses are targeted by Ransomware creators and distributors, but why? Because that’s where the money is; Because attackers know that ransomware can cause major business disruptions, which will increase their chances of getting paid; Because computer...