Cyber Security Resources
Educate your teams to protect your organisation
Cyber Security Education
Cyber security for small and medium sized businesses has never been such a hot topic. With people from throughout the business getting involved and everyone needing to understand the risks.
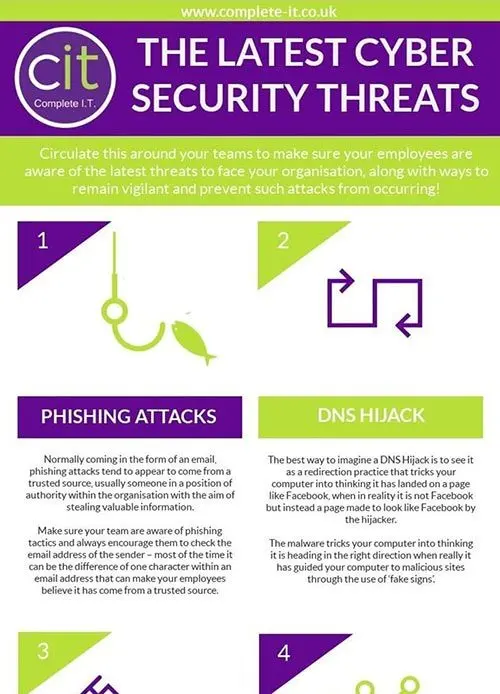
We have put together this page which is regularly updated with cyber security information and updates, on everything from how to spot a phishing email, to patch management and 2 factor authentication. Please feel free to download the assets and share with your teams.
Our PDF Downloads

Complete Firewall Protection
PDF File size: 1 MB

Complete Email Security
PDF File size: 879 KB
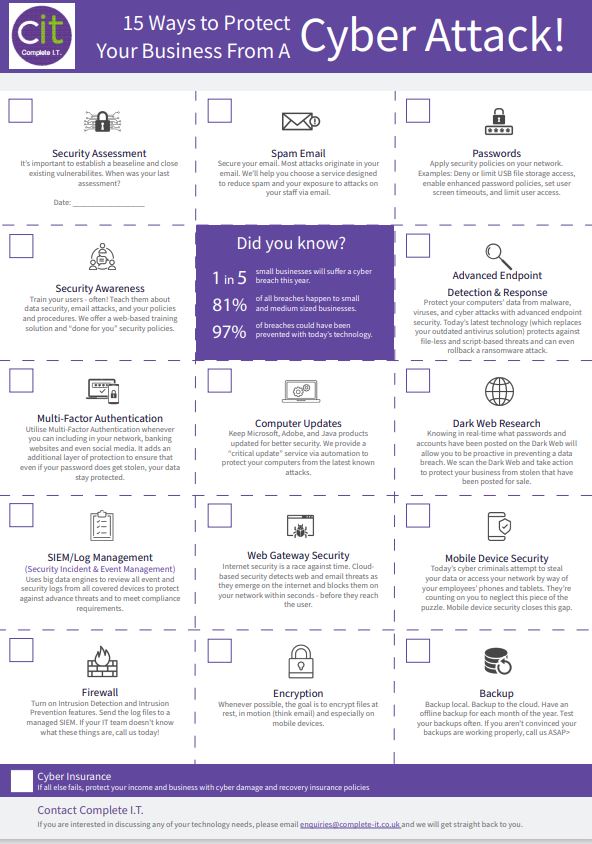
15 Ways to Protect Your Business From A Cyber Attack
PDF File size: 123 KB

Total Endpoint Security
PDF File size: 863 KB

Technology Today, Tomorrow and Beyond
PDF File size: 4 MB

Creating an effective business lan
PDF File size: 407 KB

Ransomware Report
PDF File size: 3.77 MB

Part 1: The Nature of Cyber Crime
PDF File size: 1 MB

Part 2: The Nature of Cyber Crime
PDF File size: 1 MB
Our Top Tips

5 Tips to Spot a Phishing Email

5 Tips to Stop Ransomware

5 App Tips

5 Tips to Stay Safe on Social Media

5 Reasons Why You Need to Patch

5 Tips to Create a Strong Password
Cyber Security Webinars

Cyber Security – How has it changed and what should you know?

How to Spot a Phishing Email Before it is Too Late

Understanding the Current Cyber Threat Landscape

What is Multi-Factor Authentication and why every organisation must look at rolling it out

Phishing Emails – The new and emerging way cyber criminals are working

How have SMEs embraced technology and adapted to the ‘new normal’?

The Evolution of Cyber Security and Protecting Your Data

Endpoint Security – Secure your devices no matter where they are


The Evolution of the Cyber Threat Landscape
Endpoint Security Webinar – Key Issues & Hybrid Working
60 Sec Tech
60 second videos by our very own team, designed to help educate you and your teams.
Why Are Password Managers Important?
What is and Why Do We Need 2FA?
Spam Emails 4 Things to Look out For
Have You Tried Turning It on and off Again
Why Does My Machine Sometimes Slow Down
Complete I.T. Blog
What Are the Top 5 Benefits of IT Services and Support in 2024?
In the ever-evolving landscape of technology, organisations are increasingly reliant on robust IT services and support to navigate the challenges and complexities of the digital age. As we step further into 2024, the role of an IT support provider,...
What Is Power BI: How You Can Transform Data Analysis With Power BI and AI
In today's digital age, the combination of artificial intelligence (AI) and advanced analytics has revolutionised how organisations harness the power of data for strategic decision-making. At the forefront of this transformation is Microsoft's...
Why Add Cloud Backup
With cloud computing now being the go-to as more organisations continue to move away from traditional IT infrastructure, you need to consider where your data now is and how secure it is. Many organisations using Office 365 believe that their data...